Cybersecurity and Privacy Risk Management
| Cybersecurity and Privacy | ||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|

| ||||||||||||||||||||||||||
| Sectors | Cybersecurity and Privacy | |||||||||||||||||||||||||
| Contact | Colin Dunn | |||||||||||||||||||||||||
| Topics | ||||||||||||||||||||||||||
Activities
| ||||||||||||||||||||||||||
- Authors
“The rise of the Internet of Things (IoT) and the declining costs of sensors and cloud computing are disrupting the building industry as more organizations retrofit or build out new smart buildings. There are numerous benefits of smart building technology ranging from occupant comfort and safety to improved efficiency and sustainability. However, the proliferation of smart building technology increases the risk of a cyberattack on vulnerable endpoints that need to be protected. In most cases security has not been built in when it comes to deploying smart building point solutions, thus expanding the risk exposure. Organizations must take a security-first approach to deploying smart building technology and migrate to a security fabric architecture to improve the organization’s security posture”. (IDC InfoBrief sponsored by Fortinet)
Overview of Cybersecurity Risks Associated with Smart Buildings
The big push to adopt IoT and remote connectivity has resulted in many connected buildings with insecure remote access. Building automation systems can be a vector for cyber-attacks where potential attackers gain entry to corporate networks through HVAC systems, elevator operations, lighting, water supply, alarm systems, security devices, access systems, power supply and the list goes on. Criminals gained access to Target’s corporate information systems through inappropriate credentialing to an HVAC contractor. Russia took down the Ukrainian power grid and has infiltrated much of the US energy infrastructure. Each system and device, including its multiple versions and iterations, has its own level of cybersecurity risk. The gradual elimination of human intervention in the IoT world implies a machine-to-machine (M2M) environment where all physical systems that can interconnect and intercommunicate through an IP network can be the entry point of, or victim to, a cyber breach.
In recent years, cyber security measures have often simply focused on protecting traditional information technology (IT) systems and providing tighter controls on information security in general—often aimed at safeguarding personal and corporate data. But with the rise of smart digitization technologies and the ability to extract value out of previously disconnected or “air-gapped” operational technology (OT) systems, these systems are now part of a world they weren’t originally designed for. As such, the OT environment may be plagued by misconfiguration, vulnerable embedded hardware and software, poor cyber security practices, outdated network components, and lack of general cyber security awareness.
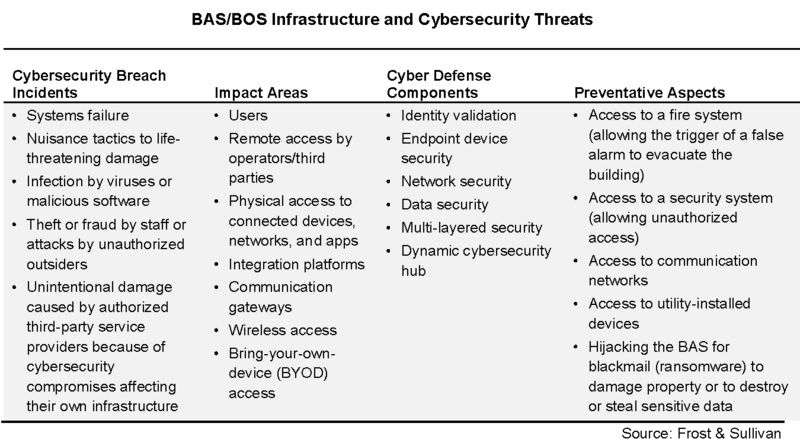
Many OT systems are experiencing cyberattacks similar to IT networks. IBM Managed Security Services (MSS) data shows a 110% increase in attacks on industrial control systems since 2016—a threat landscape predicted to grow at a phenomenal rate to 2020 and beyond. Kaspersky, a Russia-based Cybersecurity firm has issued an official warning that every 4 out of 10 automated buildings are vulnerable to cyber-attacks since the computer systems which are controlling them are affected by malware[1]. Frost Sullivan’s Building Automation System table below, illustrates some of the more common vulnerabilities.
As stated by Larry O’Brien, VP of Research at ARC Advisory Group, “there is a drive to deploy more lower cost sensors, both wired and wireless, to gather as much data as possible. At the same time, the industry has a considerable installed base of legacy building automation systems, applications, devices, and networks that must be managed, maintained, and gradually modernized.”
Review of Practical Options
Since everything is, or will soon be “connected,” what is good smart building cyber hygiene? Ongoing convergence of OT and IT systems in buildings has led to a review of the definition of physical systems within a smart building. In this regard, the National Science Foundation and NIST have attempted to classify the hybrid IT and OT systems as cyber physical systems (CPS). CPS are defined as integrated, hybrid networks of cyber and engineered physical elements; co-designed and co-engineered to create adaptive and predictive systems, and respond in real time to enhance performance. CPS is essentially coined to represent the transition and evolution in systems from industrial revolution/physical systems to the Internet revolution/cyber systems and, at present, evolving into industrial Internet revolution/cyber physical systems.
As is the case for personal and financial data, good OT / IoT cybersecurity practices start by implementing a rigorous risk mitigation strategy (identify, protect, detect, respond, recover). A key starting point is to avoid jumping into discussions of how to defend or what technologies to deploy. Decisionmakers should start with discussions of what citizen service is to be improved, and why connectivity might help advance that offering. When increased connectivity appears to be the answer, ask whether process improvement to an existing system might be more effective. At times, low-tech solutions like air-gaps and phone calls among maintenance staff may be appropriate. Other time, using the power of cloud-based predictive analytics can better inform city maintenance teams without handing control to the machines. However, some of these advancements through IoT and artificial intelligence are so compelling that the risks are worth the cost of mitigation. Cybersecurity solutions currently being offered to the smart buildings industry combine IT and physical security options, in addition to technology deployment approaches that attempt to detect anomalies and reduce vulnerabilities for IT and OT staff. In reviewing such technology options, it is important to begin by looking at a building’s critical vulnerability areas that gain top consideration.
The scale of damages in a cyber-attack can inflate significantly when open systems and converged networks are overlaid with IoT. A key attribute is the inseparable relationship of device and data brought together through aggregation in the cloud that can be compromised in the event of a cyber breach. One approach is to aggregate and encrypt data locally at the building level and not push it out to the cloud. But if the goal of deploying IoT-based systems, and “digitalizing” legacy equipment is to reduce lifecycle costs, improved asset management can only be truly achieved in an edge to cloud environment, where regular streams of integrated data drive better, more timely decisions. So, the goal should not be to stovepipe OT-derived data, but to welcome integration of these edge-based systems, while ensuring that they can’t be used as attack vectors.
Designing for the Future
As Larry O’Brien at the ARC Advisor Group puts it: “Assets are increasingly connected, driving the need for secure remote building monitoring and management. Owner-operators must also get a better perspective of the kinds of potential vulnerabilities that exist among their installed base of cyber and control system assets. Data flows must be planned and monitored, possibly making it necessary to use one-way data diodes”.
Thus IT/OT convergence is both inevitable and desirable, as it extends asset life, reduces O&M costs, increases safety and security, and improves occupants’ comfort. But as building automation systems become ubiquitous, and co mingle with enterprise-level systems, new processes and tools need to be adopted to embrace this new reality:
- Greater integration of IT and OT teams through joint management and training;
- Enterprise-wide understanding and assessment of critical assets;
- Cohesive and coordinated risk mitigation and response;
- Continuous management of all cyber-assets, vulnerabilities and threats regardless of source or vector;
- Secure building monitoring and management by “hardening” ICS, SCADA and building automation system protocols, through the combined use of hardware (data diodes[2], firewalls) and software solutions tailored to the vulnerability and criticality of asset classes.
The rise of the Internet of Things (IoT) and the declining costs of sensors and cloud computing are disrupting the building industry as more organizations retrofit or build out new smart buildings. Buildings can only be “smart” if they are safe, which increasingly implies cyber-safe. One simply needs to revisit the Target episode to understand how an attack on the HVAC monitoring system compromised credit card information of 40 million customers and other sensitive enterprise data. The number of vulnerabilities in internet-accessible ICS components across all manufacturers continues to grow while the number of devices proliferate. According to a 2018 Review of ICS Vulnerabilities by Positive Technologies, the number of vulnerabilities in the products of leading manufacturers grew by 30 percent compared to 2017. The share of critical and high-severity vulnerabilities increased by 17 percent. Furthermore, “on average, vendors take a rather long time to fix vulnerabilities (more than six months) Elimination of some vulnerabilities—measured by time from vendor notification to release of a patch—can take more than two years. For end users, such protracted responses increase the risk of exploitation of device vulnerabilities.
More than 220,000 ICS components are available online, which is 27 percent higher than in 2017. Most of them are automation system components. Such systems are mainly located in the U.S., Germany, China, France, Italy, and Canada, even though lawmakers have long been concerned about the security of such devices and systems. For example, the International Organization for Standardization (ISO) has recently published new guidance to reduce the risks of cyberattacks on machinery.” [3]
Our buildings are also visited, both physically and virtually, by those who cross many network boundaries from home to restaurants to work. These occupants include not only tenants and guests, but the staff that operate our buildings. During a crisis, such as that presented by COVID-19, we have seen teams rapidly bring together tools and approaches to keep businesses moving and keep supplies flowing… at times bypassing pre-established protocols for expediency. Access to critical systems may be tightly controlled under normal conditions, but these work-arounds can involve home computers, personal cell phones, and public wi-fi. When planning for the future, be sure to account for the resilience of staff and their willingness to be productive.
Smart building technologies offer many benefits, but also create a broader attack surface and risk due to the increased numbers of devices and connected assets. Both physical and cyber security should be at the core of any investment in smart building technology. Cybersecurity considerations and planning should be an enterprise-wide, integrated effort, involving key stakeholders, that encompasses all classes of assets connected to the internet. ICS and more broadly IoT devices are not primarily designed to be cyber-secure. Thus, they need to be integrated with security-centric technology if they are to safely deliver the promised benefits. By integrating cybersecurity considerations early in the planning stage, our connected infrastructure can best serve occupants safely and efficiently.
Next Steps…
Conducting a thorough assessment of ones’ own property which includes the building systems, other operations focused systems and platforms, third party systems and applications, communications infrastructure may seem daunting, costly and time consuming. But, as detailed above, the cost of not doing so both for one’s own operations and those of building occupants can be significant and sometimes immeasurable.
As a first next step, SBSC invites planning teams to review the Cybersecurity and Privacy Risk Management Preparation Questionnaire & Handbook. Based on the NIST Cybersecurity Risk Management Framework, it outlines core issues to watch for The Handbook portion acts as a guideline for information gathering and assessment.
Municipal citizens are intimately tied to and increasingly digitally connected to the buildings in which they live work and play. It is incumbent upon the public and private organizations that manage the broader built environment to be vigilant and diligent in their active pursuit of cyber protection.