Benefits and Cybersecurity and Privacy Risks
| Cybersecurity and Privacy | ||||||
|---|---|---|---|---|---|---|

| ||||||
| Sectors | Cybersecurity and Privacy | |||||
| Contact | Lan Jenson | |||||
| Topics | ||||||
Activities
| ||||||
- Authors
Cities and communities stand to harvest unprecedented benefits from advances in information and communications technologies (ICT), in general, and Internet of Things (IoT) and Artificial Intelligence (AI), in particular. Smart cities inevitably introduce new or heighten existing cyber risks, which demand proper consideration in design to ensure the optimal realization of intended Smart City outcomes.
Smart Cities Benefits
Smart cities are associated solutions and capabilities defined by the integration of technology, connectivity, and data to improve the quality of and accessibility to citizen services and to improve the livability of the city and community. Smart cities have the potential to address key challenges, including air and other environmental pollution, traffic congestion, crime, and economic development. Many of these challenges can be directly connected to a direct and/or an indirect fiscal impact (e.g., operational costs, lost economic productivity); conversely, Smart City solutions may have direct benefits in terms of improved services or livability as well as associated benefits of cost savings through enhanced efficiency and a boost in economic productivity, development, and opportunity.
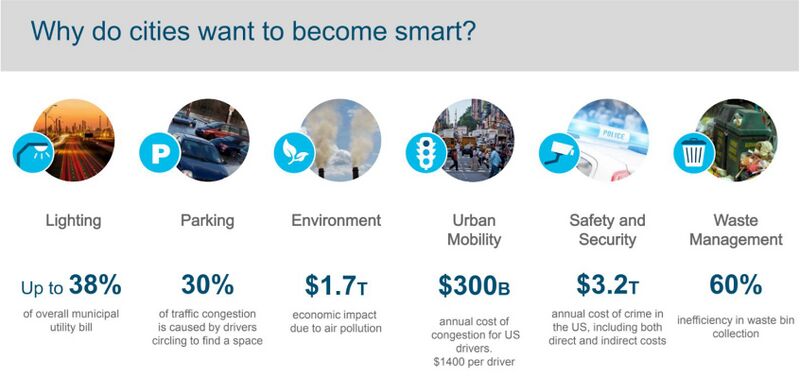

While there are many benefits associated with the promise of Smart Cities, there are also many risks and opportunities for unintended consequences. For Smart Cities to truly be successful and reach their full potential, it is important for those designing, developing, and implementing Smart City solutions to properly manage risk. Risk, in the context of Smart Cities, may be found in many common categories such as operational, financial, technical, contractual, legal, reputational, and political risk; however, one area of risk that is becoming increasingly important is cybersecurity and privacy risk. Addressing cybersecurity and privacy by design is critical to risk mitigation and enabling the successful development of Smart Cities and its benefits to citizens.
Cybersecurity and Privacy Risk
Risk (R) is commonly considered a function of three factors: vulnerability (V), threat (T), and consequence (C). While there is some contention on what the appropriate formula is, there is a clear, positive relationship between risk and each of its three variables (e.g., as consequence increases, risk increases). A common mathematical expression of risk is that risk is the product of vulnerability, threat, and consequence – or R = V x T x C.
This general notion of risk certainly applies in the cybersecurity and privacy context. With the increasing ubiquity of connectivity, cybersecurity and privacy risk is a concept that must be thoroughly considered in most, if not all, domains, including the Smart City environment. Risk in the Smart City context can be attributed to a wide variety of factors given the nearly infinite permutations of potential Smart City-related vulnerabilities, threats, and consequences.
| Example Smart City Cybersecurity and Privacy Vulnerabilities, Threats, and Consequences | ||
|---|---|---|
| Shopping List | Vulnerabilities | Threats |
|
|
|
Many of the vulnerabilities and threats that could affect Smart City environments are similar to the cybersecurity vulnerabilities and threats commonly found in the traditional enterprise information technology (IT) environment. Additionally, it is unarguable that the consequences in the Smart City context are potentially more complex and catastrophic given the cyber-physical aspects of Smart Cities as well as the broad reach and expansiveness of Smart City implementations (e.g., citizens, government, the private sector, cross-jurisdictional elements).
Moreover, it is important to recognize that cybersecurity and privacy risks to Smart City environments is not merely hypothetical or notional. Indeed, there have been several high-profile cybersecurity and privacy events (among countless data breaches and attacks around the globe) that have had real, damaging effects on some cities and communities who are leading the Smart City movement.
The following four tangible examples of Smart City cybersecurity and privacy risk are based on publicly-available information.
| Atlanta Ransomware (March 2018) | |
|---|---|
| In March 2018, the City of Atlanta, Georgia, fell victim to a SamSam ransomware attack. Government agencies were locked out of their systems, and applications and services were forced offline - in some cases for months. The attackers were asking for approximately $51,000 in Bitcoin as a ransom payment. Similar attacks were allegedly conducted in ten U.S. states and Canada - including Newark, New Jersey; the Port of San Diego; and the Colorado Department of Transportation. | |
| Vulnerability | Likely weak access control measures, which allowed a successful brute force attack (i.e., attackers guessed credentials to access system). In addition, a January 2018 audit of Atlanta’s IT systems identified 1,500-2,000 vulnerabilities in the city’s IT systems, which may have facilitated initial access to or the eventual lateral movement with the city’s infrastructure. |
| Threat | In November 2018, two Iranian nationals were charged with executing the SamSam ransomware attack; they are not considered to be associated with a nation-state actor. |
| Consequence | Hundreds of municipal online applications and services (e.g., court systems, bill payment, law enforcement ticketing) were disabled, and many data records were lost, including police dash camera recordings and legal records. Many of these functions were considered “mission critical.” Nearly 4,000 computers were locked by the ransomware. The financial cost of response, remediation, and recovery has increased from early estimates of $2.7 million to $17 million (including $6 million in contracts for security services and software updates and $1.1 million in new IT equipment). |
| SingHealth (Singapore) Breach (June-July 2018) | |
|---|---|
| For about a week during the summer of 2018, hackers actively targeted a SingHealth database and were successful in exfiltrating health-related data on 1.5 million patients. | |
| Vulnerability | A vulnerable workstation/endpoint provided the hackers with initial access. They were able to exploit privileged account credentials to access the database. |
| Threat | Singapore’s government has attributed the breach to an advanced persistent threat (APT) group from a nation-state actor. After the SingHealth breach, they determined that the hackers had been in their systems for at least 10 months. |
| Consequence | Personally-identifiable information, including demographic data, identification numbers, and some prescription medication history, was stolen. This data could be leveraged for further nefarious purposes, such as identity theft, fraud, or black market pharmaceuticals. Singapore paused all Smart Nation efforts in order to review cybersecurity and privacy practices. In January 2019, Singapore’s Personal Data Protection Commission announced fines totaling S$1M (approximately US$740,000) against SingHealth and its IT vendor. |
| District of Columbia Surveillance Camera Ransomware (January 2017) | |
|---|---|
| Shortly prior to the 2017 Presidential Inauguration, Washington, DC’s Metropolitan Police Department (MPD) discovered that nearly 70% of their surveillance cameras were malfunctioning or not operational. | |
| Vulnerability | Most likely, poor access control measures managing access to internet-connected computers/devices across the District of Columbia, each of which controlled an MPD surveillance camera, were exploited. It appears that the perpetrators had valid credentials for the compromised machines. |
| Threat | Two Romanian hackers used Cerber and Dharma ransomware to shutdown the police camera systems for four days and demanded $60,000 in Bitcoin ransom. However, it appears that they were unaware they were targeting an MPD system. |
| Consequence | 123 of 187 MPD surveillance cameras went offline just prior to the Presidential Inauguration. These hijacked government computers were used to launch and hide the source of a subsequent ransomware attack against a list of approximately 180,000 email addresses. While the actual consequence of this attack was relatively limited, this brought up concerns of potential national security concerns. |
| ForeScout Building Automation Systems (January 2019) | |
|---|---|
| In January 2019, ForeScout released research on the vulnerability of building automation systems. While these may not all necessarily be “smart” buildings, it is easy to imagine how similar risks exist across all types of buildings with building automation systems and related technologies. | |
| Vulnerability | Poorly implemented (digital) access control measures and software code weaknesses (e.g., cross-site scripting bugs, buffer overflow) are the primary vulnerabilities that could be exploited. Despite notifying the relevant vendors, more than 11,000 devices remain exposed and vulnerable. Many of these vulnerable devices are reported to be in schools and medical facilities. |
| Threat | The ForeScout researchers were able to develop proof-of-concept malware capable of exploiting these building automation systems for about $12,000 - showing that it does not require a well-resourced adversary to pose a credible threat. |
| Consequence | Potential consequences could include overheating and causing damage to data centers or providing/denying physical access to restricted/secure areas. Building automation systems have been successfully exploited in other non-experimental scenarios. |
Enabling Trustworthy Smart Cities through Risk Management
Municipal governments have a responsibility to administer their respective municipalities and to provide services to their constituents. The key value propositions of “Smart Cities” emphasize the primary municipal missions and demonstrate how they can be improved through the use of data, digital technology, and connectivity:
- Improve quality of life and livability of the community
- Foster economic opportunity, growth, and development
- Ensure public safety, security, and resilience
- Bolster community health and wellness
- Promote equitable access and opportunity
In other words, Smart Cities are intended to conduct the mission of “traditional” cities, but in an enhanced manner through the implementation of “smart” capabilities.
In leveraging data and technology to enhance government services and to ultimately mature as a Smart City, municipalities also have a responsibility to address - and build in, where appropriate - cybersecurity and privacy risk management measures. Cybersecurity and privacy risk management should be viewed not only as a requirement but also as a key enabler of Smart Cities and the municipal mission.
Addressing and implementing cybersecurity and privacy risk management in a proactive manner - and communicating those risk management practices, processes, and measures - can help demonstrate municipal responsibility and build public trust. Building trust can help increase public support for Smart City programs and projects and can promote citizen participation - a requisite for the viability of many Smart City solutions and capabilities. In turn, earned trust can help expedite the development and deployment of Smart City capabilities.
Indeed, the failure to proactively manage cybersecurity and privacy risks can be a detriment to Smart City efforts and can negatively impact the very systems intended to improve city services and citizens’ livelihoods. In the example of SingHealth, a data breach and data exposure was the catalyst for Singapore to temporarily suspend its Smart Nation activities and conduct a holistic review of its cybersecurity and privacy practices. SingHealth suffered deep monetary fines. It is certainly plausible to see how data breaches or leakages could erode public support for Smart City implementations that require the collection, processing, and storage of citizen- or community-related data. Proactively managing cybersecurity and privacy risks can prove to be more effective and cost-efficient, especially when considering the total cost of ownership and including potential costs of breach response and remediation.
Ultimately, municipalities should continue to focus on the primary mission of improving the livability of their communities; however, cybersecurity and privacy risk management should be viewed as essential supporting functions. Smart city solutions should be developed and deployed in a risk-aware manner, and cybersecurity and privacy should be included as areas of risk (alongside others, such as fiscal, environmental, legal, or contractual).
The following chapter and the supporting appendices focus on describing the key elements of a cybersecurity and privacy risk management process or program. There is no one-size-fits-all approach to cybersecurity and privacy risk management. Municipalities and Smart City stakeholders will need to determine what risk management processes and functions fit their needs the best, with the understanding that the approach to risk management will necessarily adapt and mature over time as requirements and risks change.






















