Risk Assessment and Prioritization in the Smart City Cyber Resilience Planning Process
| Risk Assessment and Prioritization in the Smart City Cyber Resilience Planning Process | |
 Service Guide | |
| Team Organizations | Cybertrust America |
| Point of Contact | Lan Jenson |
| Participating Municipalities | San Francisco CA |
| Sectors | Cybersecurity and Privacy |
| Initiative | |
| Status | Concept only Stage |
| Last Updated | January 31, 2026 |
Summary
This use case summarizes an engagement between a GCTC Action Cluster member, Adaptable Security Corp (ADA), and a California municipality, focusing on how the risk management process, with a particular focus on risk assessment and prioritization, played a critical role in the overall cyber resilience planning process. The content covered in this use case primarily aligns with the Prepare, Select, Assess, and Monitor steps of the RMF.
In this example, the California municipality has Smart City systems and initiatives that rely on existing, legacy IT infrastructure as well as stand-alone, dedicated infrastructure. The Chief Information Officer’s (CIO) office is conscious of the increasing cyber attacks, in particular ransomware, that have been waged against the public sector; as a result, they have decided to invest in cyber resilience planning for the entire IT and Smart City ecosystem. ADA has been assisting the CIO in the multi-year planning effort.
While the municipality had already adopted a comprehensive cybersecurity management plan and had already implemented the various risk management steps of Prepare, Categorize, Select, Implement, Assess, Authorize, and Monitor - albeit to varying degrees and different terminology - it was necessary to start with a risk assessment to understand and benchmark the municipality’s starting cybersecurity and privacy status. The data presented in this use case has been modified to protect the municipality’s sensitive cybersecurity and privacy information and is presented for illustrative purposes only.
Risk Assessment
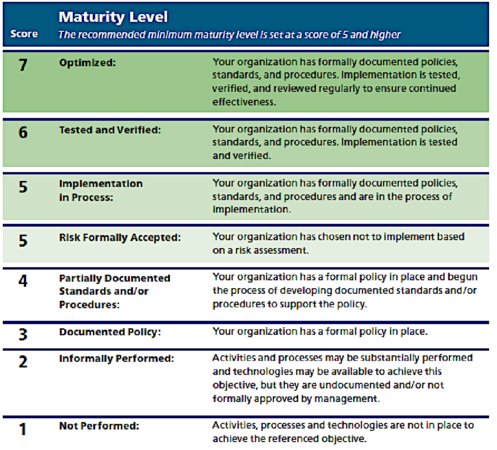
Two risk assessment methods were utilized for a high-level understanding of the municipality’s cybersecurity and privacy risk posture: the “CPAC ‘Top X’ Questions for a Trustworthy Smart City” (see Appendix C) and the Center for Internet Security’s (CIS) Nationwide Cybersecurity Review (NCSR). The former elicited much-needed background information such as the size of the municipality and cybersecurity staffing, while the latter assessed the maturity level of the municipality against 108 discrete controls. The NCSR maturity levels were based on a scale from 1 to 7, ranging from “Not Performed” to “Optimized,” respectively. Example excerpts of each assessment have been included below.
Risk Prioritization
The risk assessment resulted in two primary outputs: (1) the CIO and municipality established a vision “to enable smart, adaptable, and resilient County IT through risk-based prioritization, forward-looking security architecture, and cost-beneficial implementation;” and (2) a goal to raise the risk posture score to 5 or above (i.e., “risk formally accepted” or “implementation in process”) in every category.
To accomplish this risk prioritization exercise, ADA and the municipality quantitatively assessed and ranked specific cybersecurity controls and the associated components of risk (i.e., vulnerability, threat, and consequence - or in this case, vulnerability, threat, impact, and likelihood). The output enabled the prioritization of controls for further investigation; investing in priority controls could reduce overall risk exposure. Example risk calculations are displayed in the table below and are intended to be for illustrative purposes only.
Example Risk Score Calculation
| Control | Vulnerability Score (out of 5) | Threat | Likelihood | Impact | Risk Score (out of 80) |
|---|---|---|---|---|---|
| Cybersecurity roles and responsibilities for the entire workforce and third-party stakeholders are established | 3 | Ransomware | 92% | 4 | 35 |
| Phishing | 92% | 4 | |||
| - | - | - |
Cost-Benefit Analysis and Control Selection
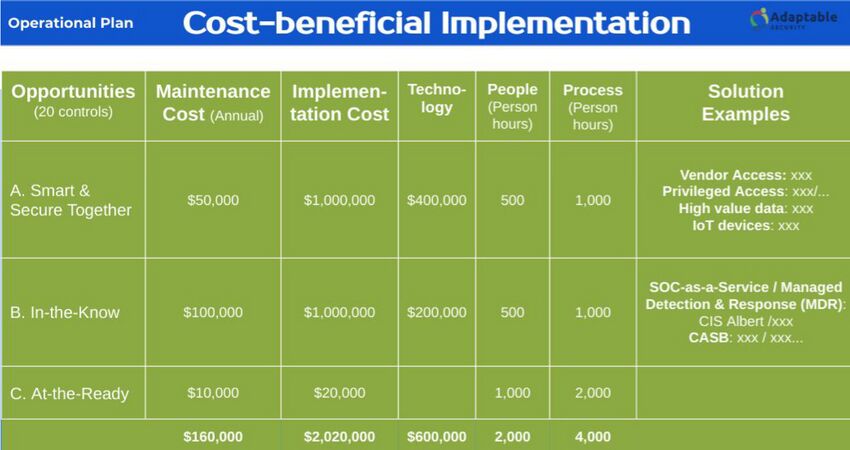
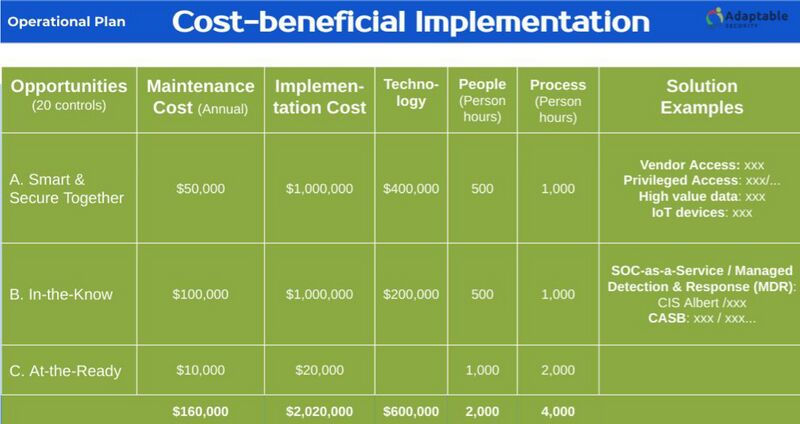
Following the risk assessment and prioritization, the next step was to identify the most economic options that would also provide satisfactory solutions to addressing the identified risks. The team adopted a model to estimate one-time implementation costs as well as ongoing annual maintenance costs. Furthermore, the implementation costs are broken down into three components: technology, people, and process; people includes consultants with specialized expertise, whereas process includes employees’ time.
The following table shows an example cost-benefit analysis where each “opportunity” represents an aggregated group of controls to address one or more identified cybersecurity or privacy risk. For example, the “In-the-Know” opportunity corresponds to a set of controls related to monitoring and detection, whereas “At-the-Ready” refers to incident response- and recovery-related capabilities.
Success Metrics
ADA and the municipality intend to regularly (e.g., quarterly, annually) monitor and measure progress in managing cybersecurity and privacy risk through three metrics:
- Overall risk posture as indicated by updated NCSR risk assessment scores
- Cybersecurity awareness survey results across key stakeholder groups
- Rating of confidence in municipality’s cybersecurity posture across key stakeholder groups
These metrics, along with the updated risk assessments, can provide indications about where risk management activities are successful, deficient, or need to be adjusted. This repeatable process of identifying, ssessing, and prioritizing risks followed by selecting, implementing, and assessing appropriate controls enables the municipality to manage their risk posture and adapt to an ever-evolving operating environment and threat landscape.