Protecting user Data in the Smart City scenario: Difference between revisions
No edit summary |
No edit summary |
||
| Line 17: | Line 17: | ||
|impacts=The benefits of this approach consider new jobs (regarding the participating developers that will work on the creation of this system) also the security improvements regarding data collection and storage due to the possibility that any public agency or any private institution will be able to implement this encryption and privacy methods on their organizations. | |impacts=The benefits of this approach consider new jobs (regarding the participating developers that will work on the creation of this system) also the security improvements regarding data collection and storage due to the possibility that any public agency or any private institution will be able to implement this encryption and privacy methods on their organizations. | ||
|demonstration=On the demonstration phase we will look at having the system up and running to provide the encryption services both to users and developers compliant with the standards and regulations of personal data protection. | |demonstration=On the demonstration phase we will look at having the system up and running to provide the encryption services both to users and developers compliant with the standards and regulations of personal data protection. | ||
|chapter=Practical Guide: IoT Cybersecurity & Privacy | |chapter=Practical Guide: IoT Cybersecurity & Privacy | ||
|supercluster=Data | |supercluster=Data | ||
Revision as of 05:00, January 25, 2023
| Protecting user Data in the Smart City scenario | |
|---|---|

| |
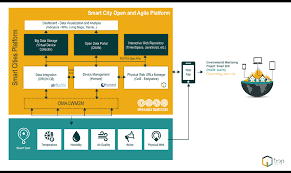 Architecture of Open & Agile Smart Cities Solutions | |
| Team Organizations | Tecnológico de Monterrey State of Mexico Campus |
| Team Leaders | Nestor Velasco-Bermeo |
| Participating Municipalities | Mexico City |
| Status | Launched |
| Document | [[File:Tech Jam Presentation|Download]] |
Description
Data is exchanged intensively within a Smart City, the correct usage of such information is vital to provide a better service to the citizens. Protecting user’s details is the key of a broader adoption of any application with intense data exchange and exploitation.
Challenges
The challenge resides on protecting user’s details (GPS position, health details/information) while at the same time being able to use it within the scope of an application.
Solutions
The proposed solution consists of an Encryption layer that allows the user to select what information he/she will be willing to share, and which details will remain private.
Major Requirements
The approach we are trying to implement is a multi-level encryption tool that will allow the user to decide which information they will share and which will be kept private. Also, a white-list approach will be tested to provide the user the possibility of selecting which kind of applications will be able to consume the user’s details without any restriction and which other applications will be blocked. The solution includes a developer’s API that will implement SOTA encryption methods before consuming and storing any data.
Performance Targets
| Key Performance Indicators (KPIs) | Measurement Methods |
|---|---|
|
Our performance targets/KPIs currently focus on anonymizing all the basic private data from users (sex, age, location) we will also focus on providing at least top of the line encryption algorithms to encrypt the generated data. Finally we will have the developers API up and running on an cloud instance that will accept petitions from any application. |
User’s data is encrypted and successfully stored, if there is any security breach the downloaded data will be useless without the proper de-cryption keys and algorithms. |
Standards, Replicability, Scalability, and Sustainability
The project will be developed using open source & royalty free applications which will ensure the sustainability and replicability. The Standards used will be according to HIPAA regarding data protection and we will also consider EU regulations regarding protecting user Data. Regarding scalability the usage of FIWARE data models will allow us the possibility of taking models built and tested by a big and strong community to ensure the integration of the solution with additional Smart City applications.
Cybersecurity and Privacy
{{{cybersecurity}}}
Impacts
The benefits of this approach consider new jobs (regarding the participating developers that will work on the creation of this system) also the security improvements regarding data collection and storage due to the possibility that any public agency or any private institution will be able to implement this encryption and privacy methods on their organizations.
Demonstration/Deployment
On the demonstration phase we will look at having the system up and running to provide the encryption services both to users and developers compliant with the standards and regulations of personal data protection.