Risk Management in a Privacy-Specific Context: Difference between revisions
No edit summary |
No edit summary |
||
| Line 1: | Line 1: | ||
{{Infobox project | {{Infobox project | ||
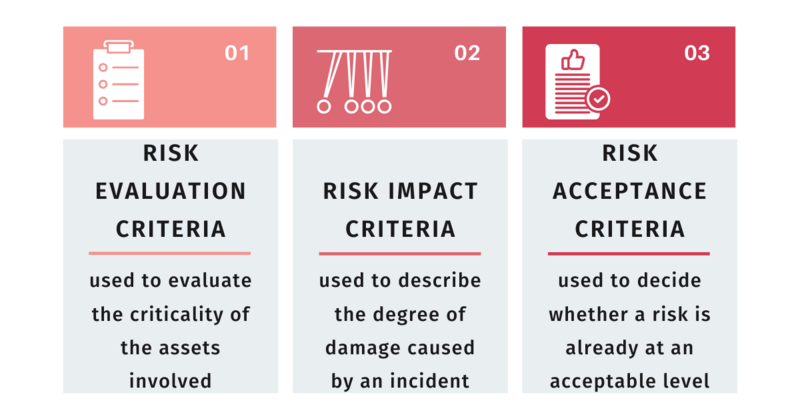
|image=Phases-of | |image=Phases-of-risk-image.png | ||
|imagecaption=Risk Management in a Privacy-Specific Context | |imagecaption=Risk Management in a Privacy-Specific Context | ||
|team-members=Cybertrust America | |team-members=Cybertrust America | ||
Revision as of 15:58, April 15, 2022
| Risk Management in a Privacy-Specific Context | |
|---|---|

| |
 Risk Management in a Privacy-Specific Context | |
| Team Organizations | Cybertrust America |
| Point of Contact | Lan Jenson |
| Participating Municipalities | |
| Sectors | Cybersecurity and Privacy |
| Initiative | |
| Status | Concept only Stage |
| Last Updated | April 10, 2025 |
Summary
This use case describes how the risk management concepts and processes presented in this Guidebook apply in privacy-specific applications. Given the overlapping relationship of cybersecurity and privacy, much of the information in this use case may sound similar to, or even identical to, aspects of cybersecurity risk management. This reinforces the notion that cybersecurity and privacy are closely related and should generally be considered in tandem. One fundamental tenet of Smart Cities is the creation, collection, use, and other methods of processing often vast amounts of data to improve city services and operations. This has the potential to introduce significant data privacy risks. Whether we are discussing individual privacy, corporate privacy, or municipal privacy, compromised data can result in tangible and irreparable damage. For example, individuals can lose their reputation, job, family, health coverage, bank accounts, or control of their identity; a company can lose its intellectual property, reputation, customer base, etc.; and a municipality can lose control of its infrastructure and supported services, whereby thousands or millions of people can be affected.
The RMF provides a process for establishing a Privacy Program to help organizations protect data over its entire lifecycle. The activities described below are not intended to be comprehensive, but rather identify some key privacy and data protection considerations.
Step 0: Prepare
- Identify employees and external resources - including privacy experts - to participate in a cross-departmental and -functional team
- Provide privacy training so that everyone knows what to look for and what to consider.
- Establish a regular process and meeting to identify all department’s data assets.
- Document what data types are processed; current data use procedures; how electronic information is handled; past problems or gaps in process; goals that may impact data types/use; employee training and experience; what systems are used to process data; and what condition those systems are in, to name a few.
- Create a table for Data Classification of the Elements. As risks associated with a data element are identified, that data element is assigned a Classification. The Classification informs the organization of the cybersecurity and privacy measures that need to be implemented and how data handling will be restricted.
- Identify and prioritize known privacy risks.
- Conduct privacy risk assessment including identifying and determining the efficacy of existing privacy controls.
- Consider strategies for implementing improvements and reducing privacy risk.
- Identify regulatory compliance requirements.
- Establish a Privacy Policy and/or Strategy to govern the organization’s privacy risk management activities and include a mechanism to routinely update the policy or strategy.
Step 1: Categorize
The types of data that are created, used, shared, viewed, stored or processed in some other way, are classified by looking at the risk consequence if the confidentiality, integrity, or availability of the data is compromised at any point in its lifecycle. A greater risk generally requires greater risk mitigation measures. What electronic systems are needed? What level of security and privacy needs to be in the system design? For example, if a system breach revealed non-sensitive floor plans we may not be concerned; if a breach revealed bank account numbers, passwords, and balances, we would be. While privacy policies and regulations might determine data classification and commensurate security and privacy controls, security technology enables data protection to the appropriate level.
Step 2: Select
What options are available to achieve the necessary controls for protecting against or mitigating the various identified privacy risks? Data of the same classification levels should be subject to similar sets of cybersecurity and privacy controls. Low risk data can be stored less rigorously, and presumably, less expensively; data of greater privacy risk may be subject to increased, and in some cases, more expensive controls.
From a privacy perspective, data can be protected through a combination of administrative (e.g., policies, procedures), technical, and physical controls. Some key privacy-centric security controls that are often considered include encryption, de-identification, anonymization, media sanitization, and geographic storage restrictions. Application of cybersecurity and privacy controls to data-at-rest versus data-in-motion versus data-in-use may also affect the selection of specific controls.
Step 3: Implement
Identify the required tasks, step by step, to implement your plan and selected controls. Document and save all system designs, architecture with data flow charts, and the data classification involved.
Step 4: Assess
An important and prevalent tool for assessing privacy risk and the effectiveness of controls is a Privacy Impact Assessment (PIA). Assessments should be conducted objectively to determine whether implementation has been completed to specification and working as intended. Any deficiencies are documented, and a corrective plan is put in place. Once corrected, another assessment should take place to ensure compliance and that the desired outcome regarding the protection of privacy is achieved. Assessors should be independent and also experienced in the data type and security systems involved.
Step 5: Authorize This step ensures accountability for a system that is designed to meet the required privacy needs. An informational package detailing all steps and outcomes is prepared, and includes responsible roles and their team names, as well as the risk assessments, privacy impact assessments, and strategy behind the decisions.
Step 6: Monitor This step involves the ongoing evaluation of the privacy risk environment to identify changes as well as opportunities to achieve the desired risk posture. Inputs can include audits, incident debriefs, survey results, a changing threat landscape, and a changing regulatory environment. This monitoring can feed the refinement of privacy policies and procedures necessary to keep pace with evolving privacy risks.